Create Vault Policies
Policies provide a declarative way to grant or forbid access to certain paths and operations in Vault. In this step, you will create a policy and then edit it to support new requirements.
NOTE: This step assumes you started the Vault server and signed in with the root token in the Web UI step.
Create a policy
Step1: Select the Policies view from the menu
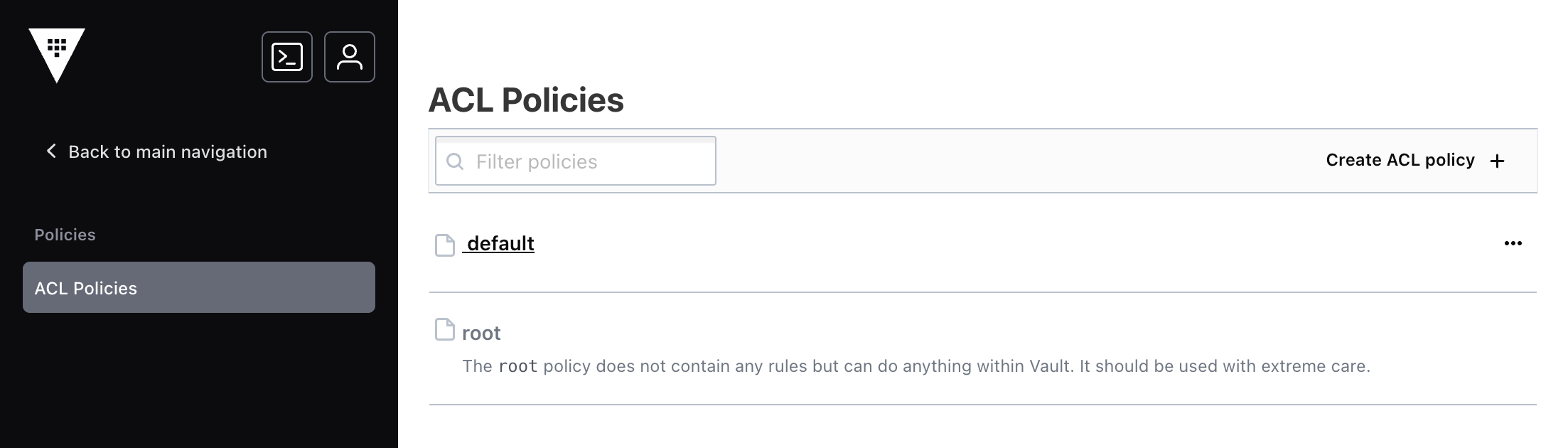
This view is the policy index and displays all the policies. The default policy and the root policy were created when Vault was initialized.
Step2: Select the Create ACL policy action.
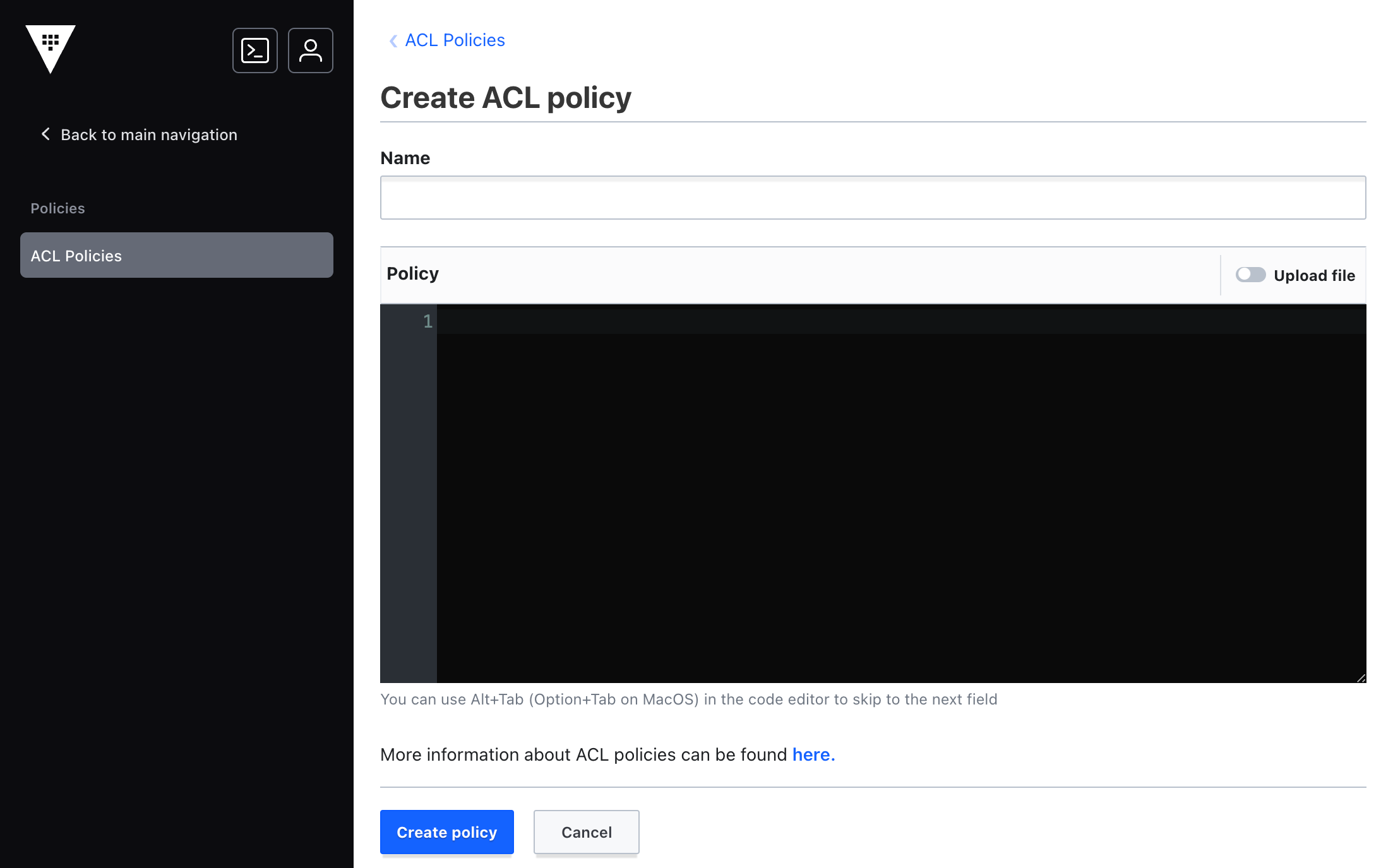
This view is the create policy view. Policies require a name. The contents of the policy can be entered through the editor or through a file.
Step3: Enter webapp in the Name field.
Step4: Enter this policy in the Policy field.
# Read the configuration secret example
path "secret/config" {
capabilities = ["read"]
}
# List secrets engines
path "sys/mounts" {
capabilities = ["read"]
}
Step5: Choose the Create policy action at the bottom of the view.
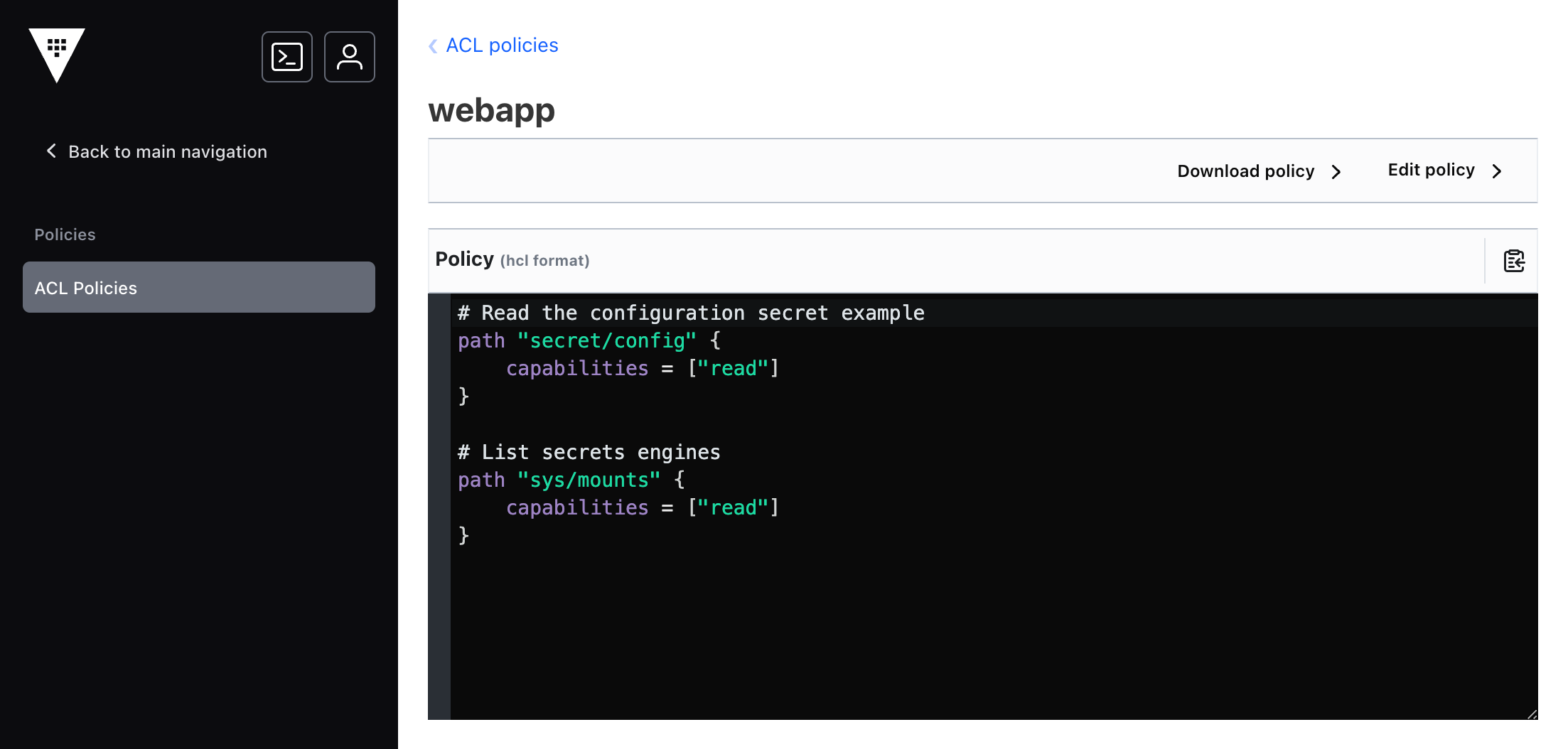
The policy is created and this view displays its name and contents.
Step6: Select the ACL Policies navigation from within the view.
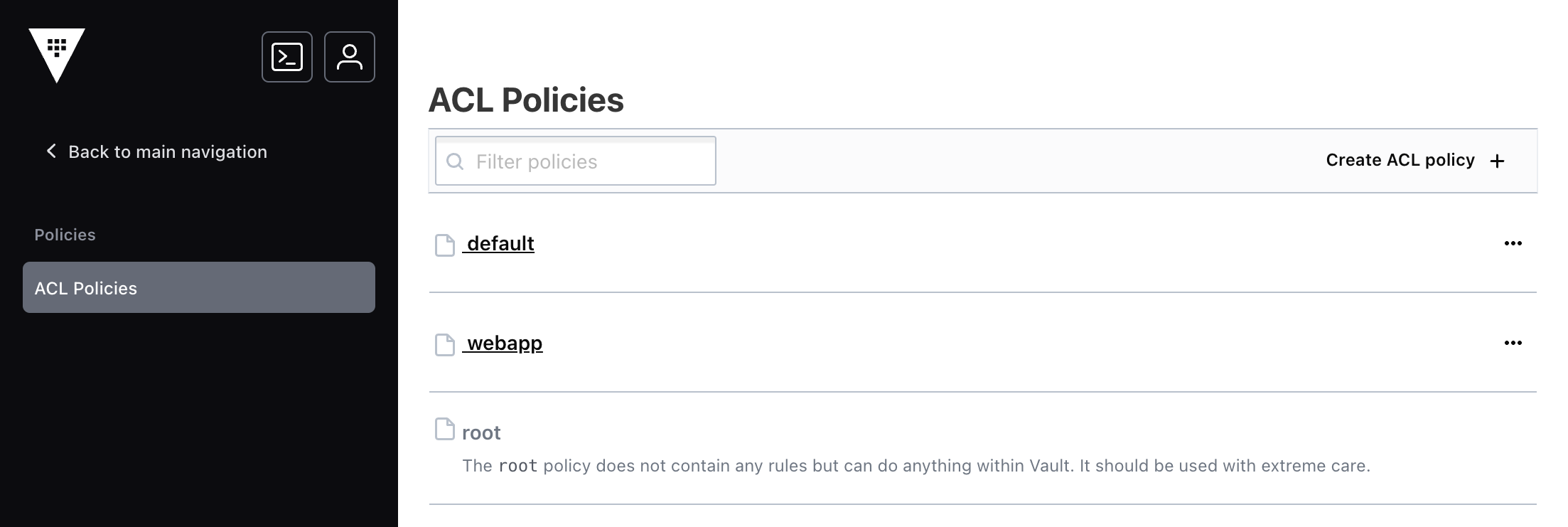
The view returns to the policy index. The new webapp policy is displayed.
Filtering: When there are a lot of policies, the Filter policies field can narrow the displayed policies down to a manageable list or the exact policy.
Edit a policy
The webapp policy needs to be updated to support a new secrets engine and its paths required and capabilities.
Step1: Select the webapp policy title from within the policy index view.
This view displays the policy with its definition. The read-only policy field displays the entire contents of the policy.
Step2: Select the Edit policy action from within the view.
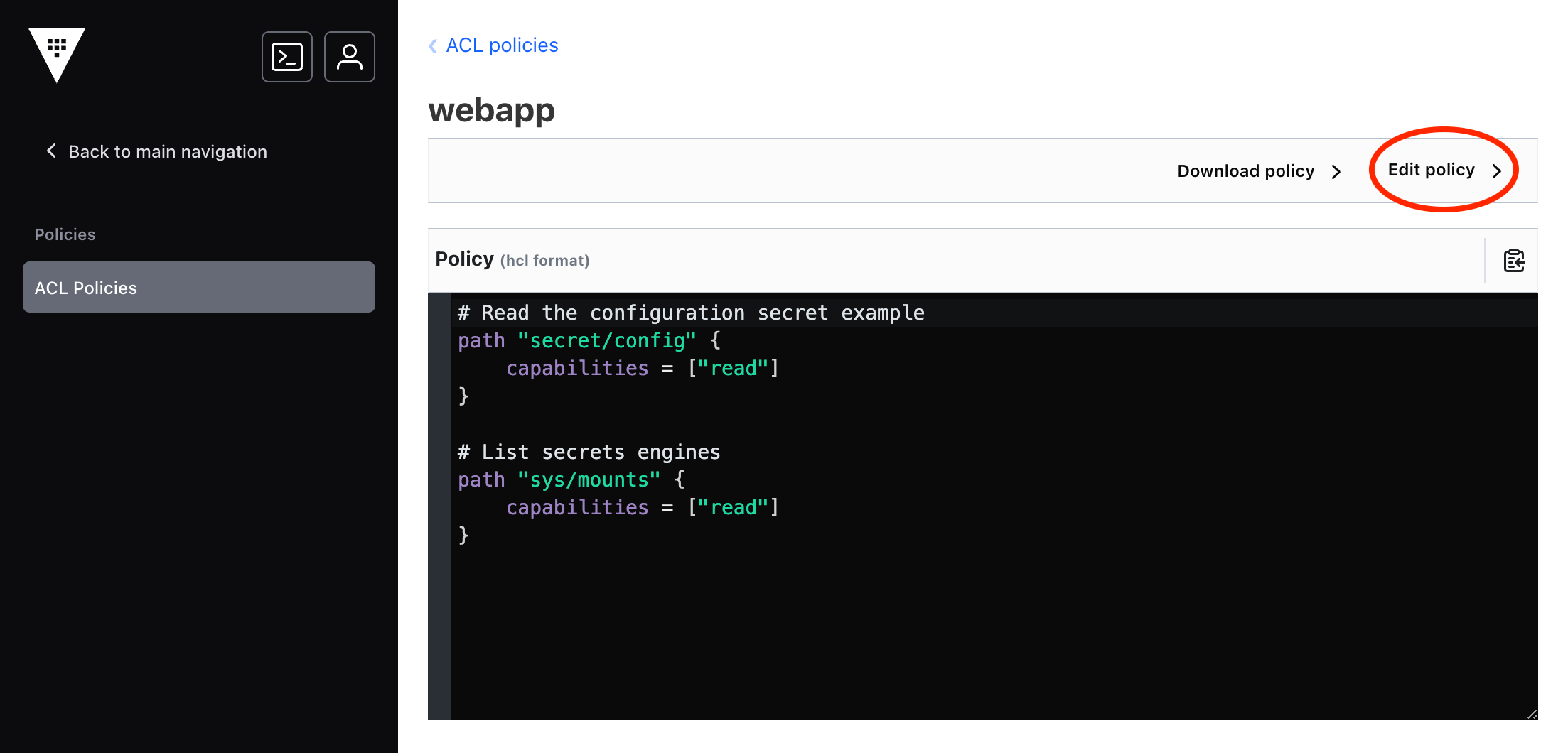
This view is the policy edit view. The Policy field provides a text editor preloaded with the policy definition.
3. Select the Policy text editor from within the view.
The editor enables navigation through the arrow keys.
4. Add this policy to after the other content in the Policy field.
# Enable Transit secrets engine
path "sys/mounts/transit" {
capabilities = ["create", "update"]
}
# Manage Transit secrets engine keys
path "transit/keys" {
capabilities = ["list"]
}
path "transit/keys/*" {
capabilities = ["create", "list", "read", "update"]
}
path "transit/keys/+/config" {
capabilities = ["create", "update"]
}
# Encrypt with any Transit secrets engine key
path "transit/encrypt/*" {
capabilities = ["create", "update"]
}
# Decrypt with any Transit secrets engine key
path "transit/decrypt/*" {
capabilities = ["create", "update"]
}
Editing Tip: The editor supports common keyboard shortcuts for undo and redo. You can also reset every change back its original by choosing Cancel.
The updated policy needs to be saved.
5. Choose the Save action at the bottom of the view.
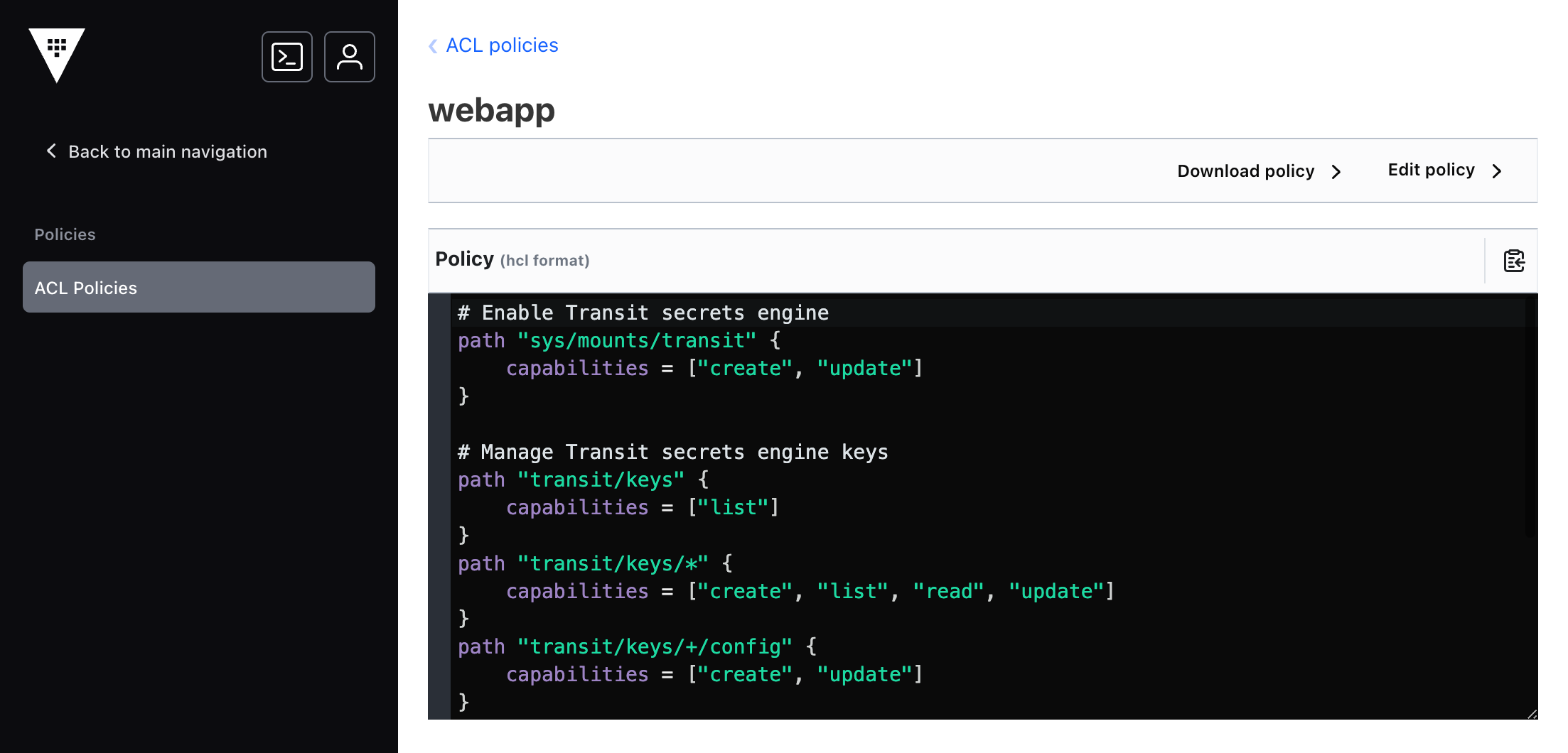
The policy is updated. The view returns to the policy and its updated definition.